Studying and learning Sql server.
Environment : Windows domain with a sql server machine.
The FE on all client PCs can access the data on sql server using DSNless linked tables. (Trusted_Connection)
Anyone from a client PC, can install SQL server management studio (or something else) and login to server.
I'm trying to learn how to disable users login to server, while they still are able to access the data from FE.
In SMS under server-->Logins I have this:
When I open BULTIN\Users property --> Status tab I have this:
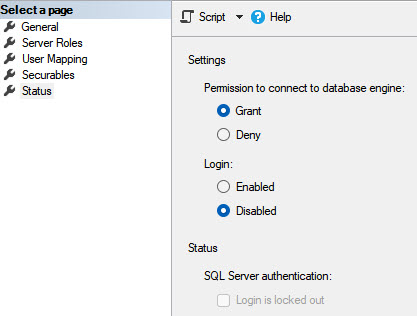
But still users can login to server from a client PC by MSM.
How can I prevent users login to sql server ? (except Domain\Admin or sa)
thanks.
Environment : Windows domain with a sql server machine.
The FE on all client PCs can access the data on sql server using DSNless linked tables. (Trusted_Connection)
Anyone from a client PC, can install SQL server management studio (or something else) and login to server.
I'm trying to learn how to disable users login to server, while they still are able to access the data from FE.
In SMS under server-->Logins I have this:
Code:
##MS_PolicyEventProcessingLogin##
##MS_PolicyTsqlExecutionLogin##
BUILTIN\Users
Domain\Administrator
NT AUTHORITY\SYSTEM
NT Service\MSSQL$SQLEXPRESS
NT SERVICE\SQLTELEMETRY$SQLEXPRESS
NT SERVICE\SQLWriter
NT SERVICE\Winmgmt
saWhen I open BULTIN\Users property --> Status tab I have this:
But still users can login to server from a client PC by MSM.
How can I prevent users login to sql server ? (except Domain\Admin or sa)
thanks.
Last edited:

