"Welcome" to AWF

Sad to see that you've moved from UA just to persist in making incorrect statements.
For info, this post relates to my
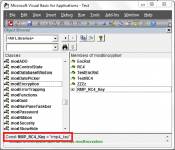
Encrypted Spilt No Strings example database / security challenge
With a lot of help from me AND a huge amount of time and effort on your part, you made some limited progress in hacking the app.
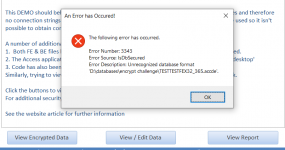
However, you showed no evidence that you had actually decrypted the data to plain text.
At my request you sent me the Excel file which clearly indicated that you had just copied the decrypted data manually.
For those unaware of the app, the decrypted data is available for editing in the FE.
In recent weeks, you have made repeated false claims regarding the security of Access files including statements that ACCDE files could easily be reverse engineered to ACCDB and that ACCDB/ACCDE encryption passwords could easily be bypassed.
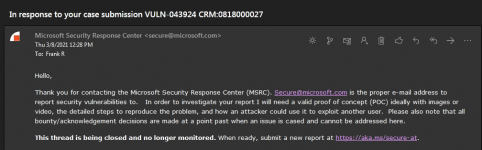
You have also forwarded my example app to the
Microsoft Bounty Programs | MSRC without my permission. Whether that was to try and get a reward or to alert them to supposed weaknesses in Access isn't the point. You had no right to do so without asking me first.
If there are any weaknesses in the app, these are due to my errors rather than Microsoft.